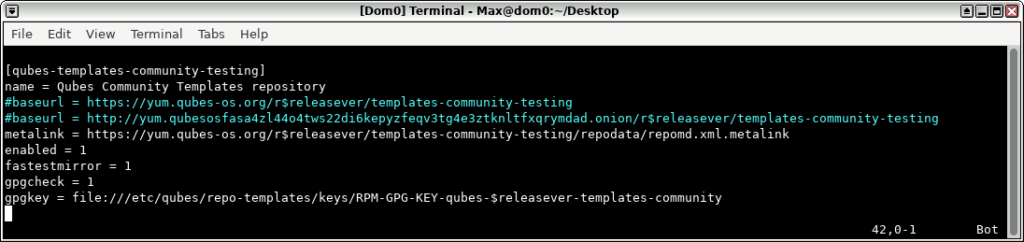
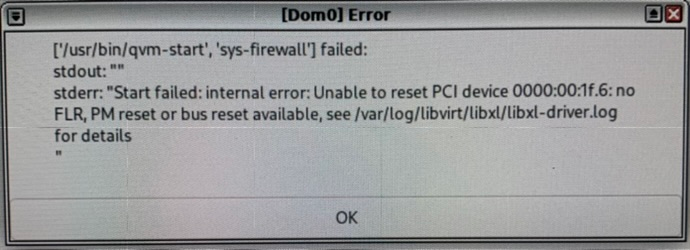
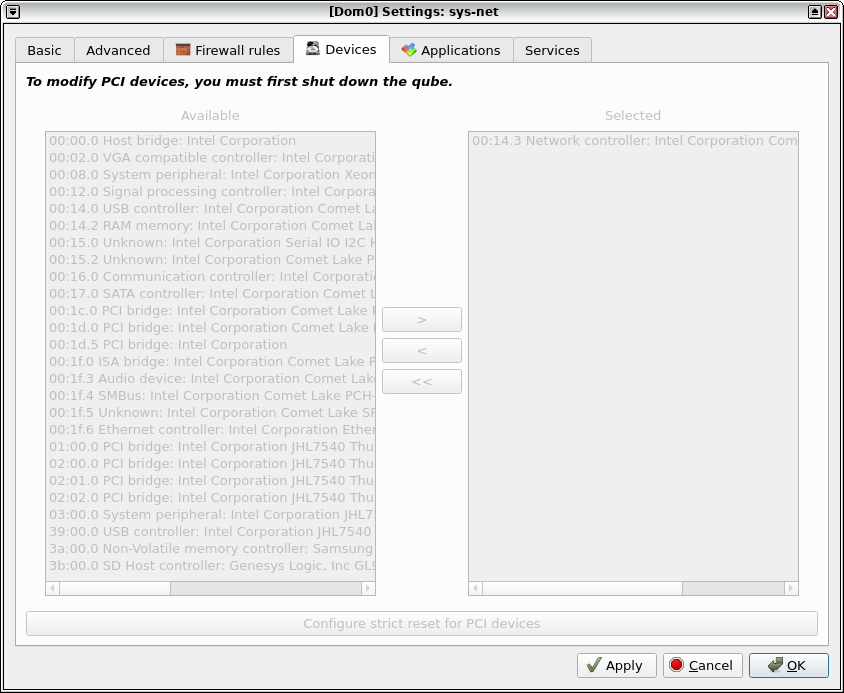
Why evaluate yet another password manager, when so many exists and what are my requirements for a decent one?
First:
- My password manager must be locally accessible
Why:
- I don’t want to input my “Master” password to all my passwords directly on a frontend on the internet (That includes API’s, etc.) Frontends get compromised all the time and with E2E encryption, the actual decryption is on the frontend. That means that I would never trust a SaaS password manager solution. Risk acceptance declined (Accepting the risk!)
Next:
- My password manager database must be synced across devices (minimum desktop/laptop + phone).
Why:
- Because syncing is needed if I use more than one device (and most of us do!) and the synchronization is only performed on encrypted file, so no cloud provider can read it in clear text. And yes, my iPhone is in Lockdown mode, always, hopefully helping my device to be more protected than if not.
and finally:
- My password manager needs a web browser plugin
Why:
- I might have one database for low-risk passwords accessible via browser-plugin, and another high-risk passwords only in airgapped VM., depending on risk acceptance.
So with that out of the way, let us test Enpass to see what solution is up to par. It actually seems like this password manager is the only one meeting my requirements(?):
Installing Enpass
My taste in installation on Linux is using either the distribution’s own repositories(RedHat) or if you trust the supplier of the software more, their repositories(Enpass). If you fear supply chain attack, you might want to install a package and not update it, if you trust the source code and needs to review it, continuously. For me, the application needs to get updated when I update my other packages using an update app or via dnf update og apt update.
I even prefer updating before official releases, when related to security (Link to Risk analysis on KeePassXC):
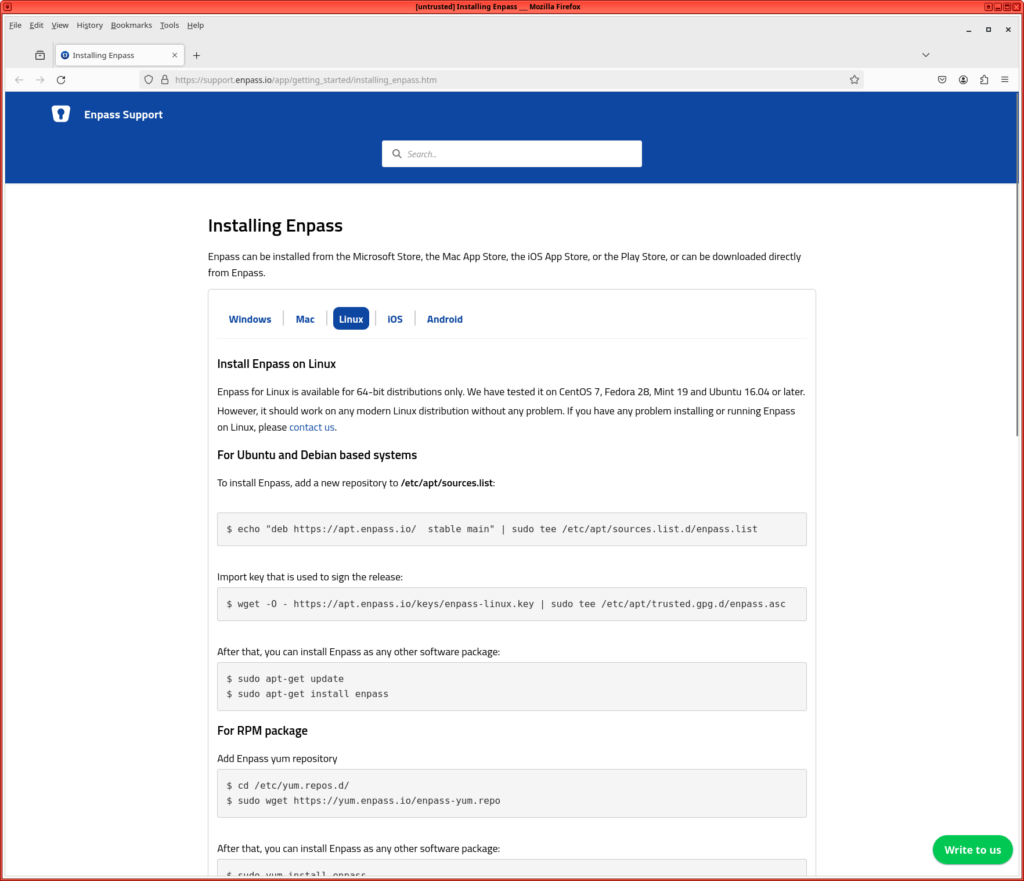
Add the repositories, install wget and the application using the instructions on the link above:

The above installation creates the executable in /opt/enpass/Enpass which is so correct it is not always included in path, so might only work when directly addressed or a symlink is created.
https://www.qubes-os.org/doc/app-menu-shortcut-troubleshooting/
Start the app and select “Folder Sync” and select your Dropbox Folder, that is already being synced. If you want your password manager to sync itself, feel free to insert a dropbox account as per below “Dropbox” or any other file syncing service:

Set your master password, press continue and retype:

Confirm your Master password:

Then you get the possibility to install browser extensions, so press the install button, if you trust it to be safe.
This might have implications beyond my knowledge and if you are hit by a 0-day in your browser, the password database might be compromised by a browser plugin, I suspect. So evaluate your risk acceptance again. Remember: you can always copy / paste with clipboard between VM’s anyway(if you are using QubesOS with airgapped Password Manager VM):
And click “Get it” to install the extension:

Click “Continue to installation”:

Click “Add” if you trust Enpass with your browser data:

And your password manager plugin was added. Click Okay.

Then set Enpass as the default password manager or do it yourself. Choose deny or allow to your preference.
A great way to avoid re-using compromised passwords, even if not used by you, but by others, thereby also being used in password spraying attacks, etc. enable the “Check Compromised Passwords”:

Activate it using your email:

And type in the code sent to your email:
Conclusion:
It clicks my 3 boxes, so I might switch from my “KeePassXC / KeePassium” setup to this software if I trust the company over time.
Sometimes you can buy a license with a great discount for the first year. “International Womens Day”, had a 66% discount, so you might wanna wait to purchase at the right time.
high-risk passwords should be in an airgapped database.
low-risk passwords should be installed as shown above in a user-friendly database, syncing all passwords in cloud and avoiding direct master password input at cloud provider.
Enpass is an indian company and my year long experience with Password Manager Pro from ManageEngine, I would not trust the code quality to be top-notch regarding security (issues have been found and I bet there are hundreds more…. Link). But do a quick risk assessment on your setup. Your phone and desktop needs adequate protection. Can’t blame it on Enpass if you have easy access to your phone from evil APT’s. And Enpass might be quality code now…. ;).