Goal: If a new security vulnerability is found in KeePassXC(eg. 0-day), I would like to ensure the fastest possible update, risking the possibility of not being able to use the application.
By updating from an unstable repository, this can, of course, also introduce vulnerabilities, that has just not been detected yet.
I have decided to rather patch known vulnerabilities, using software with potential unknown vulnerabilities, rather than having unpatched known vulnerabilities. That is basically my risk analysis.
Also, if the application fails and is unusable, it might still be better using “forgot password” features, than using a piece of known insecure software. Depends on who you are, and what level you are comfortable with. Every decision needs to be risk based and subjective to the risk taker.
So, lets solely, enable KeePassXC packages, getting updates from a more unstable branch. Put this in your fedora-30 /etc/yum.repos.d/fedora-updates-testing.repo end of first paragraph:
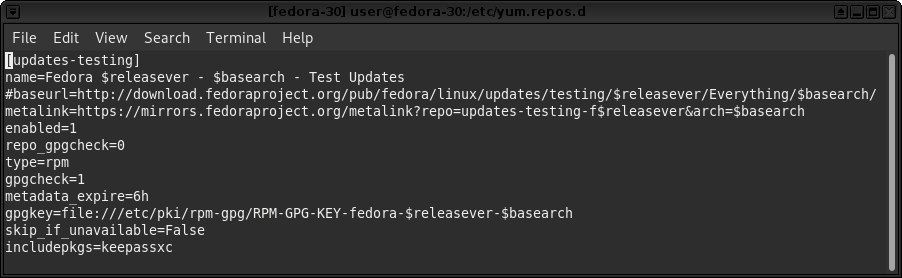
This should be called the frog/rabbit method, since we are litterally jumping ahead of ourselves, just as the remark from Quentin Tarantino in “Four Rooms” movie, states.
And I need ALL testing packages, that actually works, ending up in stable. That’s a premise.
UPDATE: As Samuel Sieb described, it is important to have “–disableexcludes” on the commandline, every time you need to update a package from the testing repository. I just experienced, I could not update the 0-day emergency patch from mozilla to firefox, due to this.
SOLUTION: [user@fedora-30 yum.repos.d]$ sudo dnf upgrade –enablerepo=updates-testing –disableexcludes=updates-testing –advisory=FEDORA-2020-2713adc57f

